How Operational Risk Management Safeguards Your Business from Unexpected Threats


Frontline workers face unique challenges that traditional risk methods often miss. Field workers, technicians, mobile teams, and other non-desk employees operate in environments where risks change rapidly, yet they often can't easily report hazards or receive critical updates. What’s more, they often spot problems first, making it crucial that they have effective ways to raise concerns.
This guide uses proven frameworks, including the U.S. Navy's methodology and ISO 31000, to help you build an effective operational risk management program for today's diverse workforce. Good risk management delivers clear results: fewer incident losses, better regulatory compliance, improved efficiency, and safer workplaces.
Whether you're creating your first risk register or strengthening what you have, you'll find practical strategies to protect your operations and empower your team through effective operational risk management.
What is Operational Risk Management?
Operational risk management is the practice of identifying, assessing, and mitigating risks that could disrupt your business, damage your reputation, or harm your employees. From human error and technological failures to process gaps and external threats like natural disasters, operational risk management covers a broad spectrum of challenges.
Without a solid operational risk management approach, including strict SOP compliance, your organization remains vulnerable to preventable incidents that can lead to costly downtime, regulatory penalties, and compromised safety. When implemented effectively, operational risk management creates a foundation for sustainable operations that protects both your people and your bottom line.
Build a Foundation for Operational Risk Management
These prerequisites align directly with operational risk management's core objectives: protecting people, safeguarding assets, and ensuring health and safety compliance. Before moving forward, confirm that your leadership has committed to the program, your governance includes frontline voices, your reporting tools reach all workers, and your culture encourages open risk communication.
Get Top-Down Buy-In
Before jumping into operational risk management, you need to lay the groundwork with executive sponsorship that goes beyond getting leadership buy-in. The idea is to establish clear boundaries for your entire operational risk management program and get folks on board with your risk-appetite statement.
This statement defines what levels and types of risk your organization accepts, creating guardrails that guide decisions at every level. When frontline supervisors face time-sensitive choices, they can use this documented appetite as their reference point.
To execute on this statement, build a cross-functional governance team with voices from operations, HR, safety, and IT. Include frontline representation such as supervisors or team leads who understand daily field realities. This diversity becomes crucial when managing risks across desk and non-desk environments since each faces distinct operational challenges. A diverse team will ensure operational risk management policies stay practical rather than theoretical.
Make Your Program Accessible to Non-Desk Workers
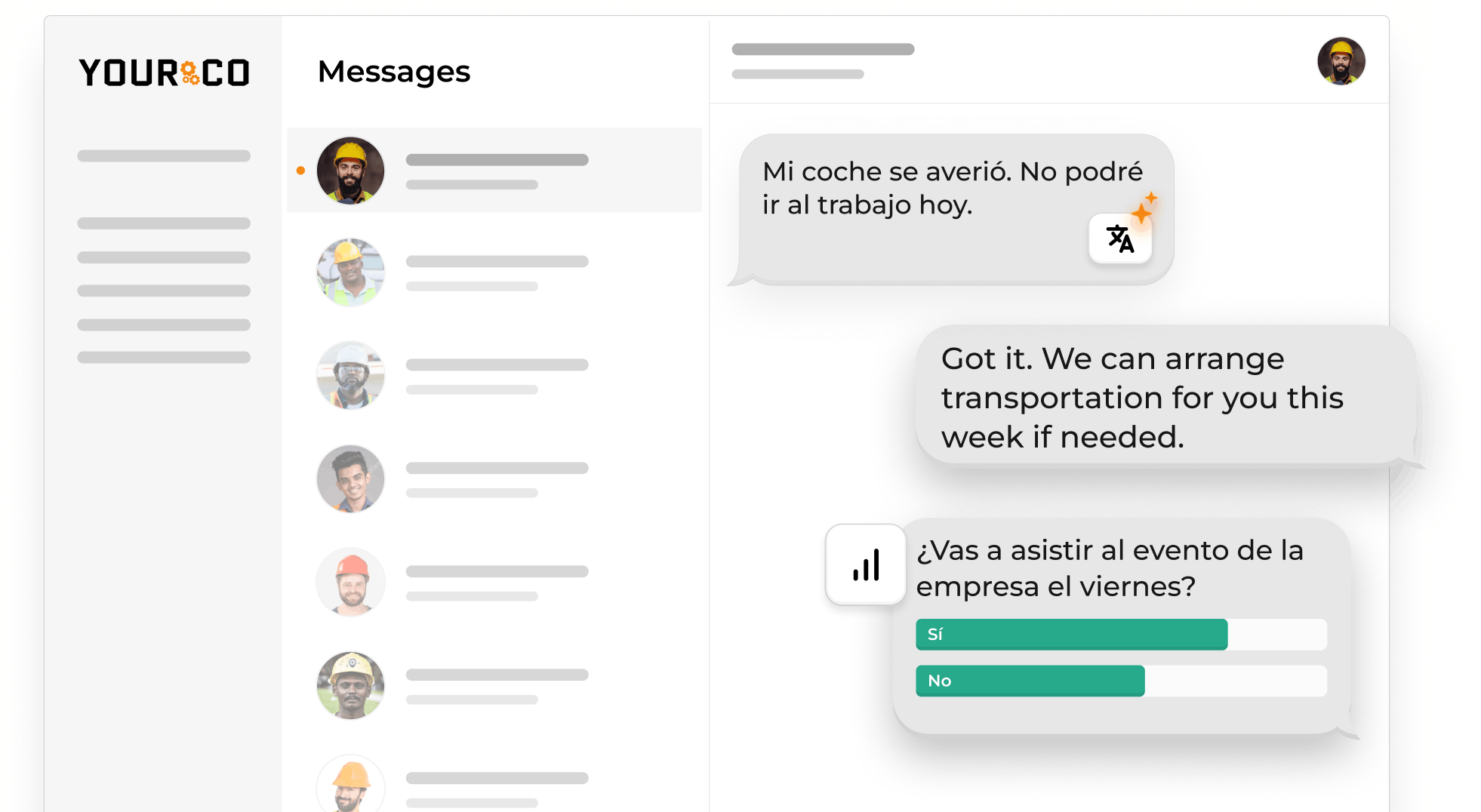
Your data collection and incident-reporting tools form the program's nervous system, but accessibility matters most. Desk-based employees might easily access company portals, but non-desk workers need different solutions, such as communication tools for deskless workers. Organizations find SMS communication particularly effective for frontline teams without regular computer access. Mobile incident reporting tools increased hazard reporting by 40% in construction settings, showing how accessible reporting channels drive results.
Listen and Reward Candor
Cultivate a culture that rewards transparency over punishment. Non-punitive reporting policies and recognition programs for risk identification create environments where people speak up freely. When your maintenance technician spots potential equipment failure or your delivery driver notices recurring safety hazards, you want them to report immediately, not hesitate from fear.
Step 1 – Identify Operational Risks
Operational risk represents the potential for loss from inadequate processes, people, systems, or external events. Unlike financial risks, operational risks exist in your day-to-day activities. Teams with many non-desk workers often face these risks in more immediate and visible ways, making early identification crucial.
You can categorize operational risks into four main buckets:
- People-related risks include human error, skill gaps, inadequate training, or malicious actions.
- Process risks emerge from inadequate procedures, control failures, or poorly designed workflows.
- Technology risks cover system outages, cybersecurity incidents, data corruption, or equipment failures.
- External events such as natural disasters, regulatory changes, supply chain disruptions, or vendor failures, which necessitate strong crisis management strategies.
Different industries face distinct operational risk profiles. Manufacturing environments might encounter machine breakdowns, safety incidents, or quality control failures. Logistics operations typically grapple with late shipments, vehicle accidents, cargo theft, or driver fatigue. Construction sites present risks from equipment misuse, fall hazards, weather-related delays, or inadequate safety protocols. Healthcare settings must manage medication errors, infection control breaches, equipment malfunctions, or patient safety incidents.
Effective hazard identification combines multiple techniques to capture both obvious and hidden vulnerabilities. Process mapping helps visualize where breakdowns might occur, while incident data mining reveals patterns from past events. Your frontline employees offer a real goldmine of risk intelligence because they encounter potential hazards daily. Risk workshops that include non-desk workers provide insights that desk-based analysis completely misses.
Enter every identified risk into a centralized risk register that serves as their risk intelligence hub. This living document captures the risks themselves, their sources, potential impacts, current controls, and assigned owners. Without this systematic documentation, even the best risk identification efforts become scattered and ineffective.
Use SMS and Mobile Tools for Easy Reporting
Mobile reporting tools, mobile workforce scheduling, and SMS-based hazard reporting systems represent game-changing technologies for non-desk environments. These platforms enable immediate, on-the-ground reporting even for workers without smartphones or regular internet access. SMS-based systems work on any mobile device, ensuring everyone can participate regardless of tech comfort level.
Process flow diagrams and failure mode analysis help you visualize how work gets done and where it might go wrong. By mapping critical processes, you can identify dependencies, bottlenecks, and single points of failure that might not be obvious during normal operations.
Apply Risk Taxonomies and Categorization Frameworks
A structured schema will provide consistent language for describing and classifying risks across your organization. When everyone uses the same terms and categories, you can more easily identify patterns, benchmark against industry standards, and ensure comprehensive coverage during risk workshops.
Leading indicator monitoring shifts your focus from reactive incident reporting to proactive risk spotting. By tracking metrics that typically precede problems, such as near-miss reports, equipment maintenance delays, or training completion rates, you can identify emerging risks before they cause actual incidents.
Example Risk Register Entry for Operational Risk Management
A well-structured risk register entry provides all the information needed to understand, assess, and manage each identified risk. Here's a practical template with a completed example from a logistics operation:
Risk ID: LOG-001
Risk Description: Delivery vehicle breakdown during peak delivery hours causing customer service delays and potential driver safety issues
Risk Source Category: Technology/Equipment
Risk Owner: Fleet Operations Manager
Initial Likelihood Assessment: Medium (occurs 2-3 times per month)
Initial Impact Assessment: High (affects multiple customer deliveries, overtime costs, driver safety)
Current Controls: Preventive maintenance schedule, backup vehicle availability, driver communication protocols
Risk Status: Active - Under Review
Next Review Date: Quarterly review scheduled for March 2024
The clear descriptions and specific ownership assignments in this example create accountability for each risk. The initial assessments provide a starting point for prioritization, while documenting existing controls helps you understand your current risk position. Regular review dates ensure that risk information stays current as conditions change.
Step 2 – Assess & Prioritize Operational Risks
Once you've identified potential operational risks, you need to assess their severity and prioritize them for action. Risk assessment involves determining both the likelihood of occurrence and the potential impact if the risk materializes. This evaluation helps you focus your limited resources on the most critical risks that could significantly affect your operations.
The risk assessment process follows four key steps:
- Determine Likelihood: Evaluate how likely each identified risk is to occur.
- Assess Impact: Assess the potential impact if the risk materializes.
- Calculate Risk Score: Combine likelihood and impact measurements to generate a risk score.
- Prioritize Risks: Prioritize risks based on these scores while considering your organization's risk appetite.
The assessment process becomes particularly valuable when you include frontline perspectives, as non-desk employees often have the most direct experience with operational realities. Their insights can reveal nuances that desk-based managers might miss, making your risk assessments more accurate and actionable.
Look Beyond Financial Impact
When assessing impact, consider multiple dimensions beyond just financial consequences. Safety impacts affect employee wellbeing and can result in injuries or fatalities. Operational impacts disrupt business processes and productivity. Reputational impacts damage your organization's standing with customers and stakeholders. Regulatory impacts can result in fines, sanctions, or compliance issues. This comprehensive view ensures you don't overlook risks that might seem minor in one dimension but could be catastrophic in another.
Remember that risk assessments aren't static documents. You should review them periodically, especially when operational conditions change, new regulations emerge, or significant incidents occur. This ongoing reassessment ensures your risk priorities remain current and relevant to your actual operating environment.
Use Qualitative and Quantitative Assessments
You have two primary approaches for conducting risk assessments, each with distinct advantages and appropriate use cases. Understanding when to use each approach will help you develop more effective operational risk management strategies.
Qualitative Assessment uses descriptive scales such as low/medium/high or numerical ratings like 1-5 to evaluate risks. This approach relies heavily on expert judgment and the experience of your team members, making it particularly suitable for initial assessments or situations where historical data is limited. For example, you might use qualitative scales similar to the Navy's "Mishap Severity Categories and Mishap Probability Levels" to categorize risks based on professional judgment rather than statistical analysis.
Quantitative Assessment takes a more numerical approach, using statistical analysis and historical data to calculate specific risk values. Common quantitative methods include Annual Loss Expectancy (ALE) calculations and Value at Risk (VaR) models. While this approach provides more objective measurements, it requires reliable historical data and sophisticated analytical capabilities that may not be available in all organizations.
Many organizations find success with a hybrid approach that combines both methods. You might start with qualitative assessments to quickly identify and categorize risks, then apply quantitative analysis to your highest-priority risks where you have sufficient data. For non-desk environments, qualitative assessments paired with short, mobile-enabled surveys can be particularly effective for gathering risk perceptions from frontline staff who are closest to the actual operations and hazards.
Build a Risk Matrix for Operational Risk Management
A risk matrix provides a visual tool for plotting and prioritizing risks based on their likelihood and impact scores. Creating an effective risk matrix requires careful planning and clear definitions that your entire team can understand and apply consistently.
Start by defining your likelihood scale, typically using a 1-4 or 1-5 point system. For example, a 4-point scale might include:
- 1 = Rare (unlikely to occur)
- 2 = Unlikely (could occur occasionally)
- 3 = Likely (expected to occur regularly)
- 4 = Almost Certain (occurs frequently)
Next, define your impact scale across multiple dimensions, using similar numerical ranges to rate the severity of consequences in areas like safety, financial loss, operational disruption, and reputational damage.
Create your matrix grid by plotting likelihood on one axis and impact on the other. Multiply the likelihood score by the impact score to generate risk scores for each identified risk. For instance, a risk with likelihood 3 and impact 4 would receive a risk score of 12. Use color coding to create zones within your matrix:
- Red zones for high-priority risks requiring immediate attention
- Amber zones for medium-priority risks needing planned mitigation
- Green zones for low-priority risks that can be monitored with minimal intervention
Establish clear thresholds for risk acceptance based on your organization's risk appetite. Plot each identified risk on the matrix using its calculated scores, which creates a visual heat map showing where to focus your attention and resources. This visual representation makes it easier to communicate risk priorities to stakeholders and track changes over time.
Understanding the difference between inherent risk (before implementing controls) and residual risk (after controls are in place) helps you measure the effectiveness of your mitigation efforts. Additionally, distinguish between time-critical assessments needed for immediate operational decisions and deliberate assessments used for strategic planning. For non-desk environments, consider creating simplified, mobile-friendly versions of your risk matrix that frontline teams can easily use during their daily operations.
Step 3 – Design & Implement Operational Controls
Once you've identified and assessed your operational risks, the next step involves implementing controls to mitigate them. This phase translates your risk analysis into concrete action, creating safeguards that protect your people, processes, and operations. Effective controls should match the risk level they address and remain cost-effective to implement and maintain.
Establish a Control Hierarchy
The most systematic approach to control selection follows the established control hierarchy, which prioritizes the most effective risk mitigation strategies first. Start by eliminating the hazard entirely whenever possible, removing the source of risk completely. When elimination isn't feasible, substitute the risky element with a safer alternative. Engineering controls come next, involving physical safeguards and design modifications that reduce exposure to hazards.
Administrative controls represent the fourth tier, encompassing procedures, training programs, and operational rules that guide safe behavior. For non-desk environments, these controls benefit significantly from real-time emergency communication systems. SMS-based platforms can automate urgent employee SMS alerts to frontline workers, ensuring critical information reaches employees immediately, regardless of their location or access to traditional communication channels.
Personal protective equipment (PPE) serves as the final line of defense in this hierarchy. While essential, PPE should never be your primary control strategy since it relies entirely on consistent human compliance and proper maintenance.
Many high-priority risks require multiple controls working together, creating layered protection. For example, a manufacturing facility might eliminate certain chemical hazards, engineer ventilation systems, implement strict handling procedures, and require respiratory protection for any remaining exposure scenarios.
Before full deployment, test all controls to verify their effectiveness under real operating conditions. This testing phase often reveals implementation challenges or gaps that weren't apparent during the design phase. Comprehensive training for all affected employees is equally important—they need to understand not just what to do, but why these controls matter for their safety and the organization's success.
Evaluate Your Mitigation Strategies
Selecting the right controls requires evaluating multiple factors to ensure your mitigation strategies actually work in practice. Effectiveness tops the list—the control must demonstrably reduce the risk to acceptable levels. However, the most effective control on paper means nothing if you can't implement it practically in your specific environment.
Feasibility considerations include whether your workforce has the skills to implement and maintain the control, whether your current infrastructure can support it, and whether it fits within your operational constraints. A sophisticated automated system might be highly effective but useless if your field teams lack the technical expertise to operate it reliably.
Cost-benefit analysis helps you allocate limited resources wisely. Calculate both the upfront implementation costs and ongoing maintenance expenses, then weigh these against the potential losses the control prevents. Remember to consider indirect costs like productivity impacts and training requirements.
Compatibility with existing operations often determines whether a control succeeds or fails. Controls that disrupt established workflows or conflict with other safety measures create confusion and resistance. The best controls integrate seamlessly into current processes, making safe practices the natural and easy choice.
Employee acceptance plays a crucial role, especially for non-desk environments where supervisory oversight is limited. Frontline workers often ignore or circumvent controls they view as impractical or burdensome. Involving frontline staff in control design and selection dramatically improves buy-in and effectiveness.
Timeliness matters when you're dealing with high-priority risks that require immediate attention. Implementing emergency preparedness strategies can be crucial. Some controls can be implemented quickly as interim measures while you develop more comprehensive long-term solutions. Digital checklists accessible through basic mobile devices, rapid incident escalation protocols, and bite-sized safety training modules designed for field consumption often serve as effective quick-deployment controls for frontline teams.
Document Operational Controls
Proper documentation transforms good intentions into accountable action. Clear records prevent even the best-designed controls from drifting, degrading, or disappearing entirely as personnel change and organizational memory fades. You should create control documentation that provides a clear roadmap for implementation and ongoing management.
Define the control objective: Begin each control record with a clear objective statement that explains exactly what risk the control addresses and what outcome it should achieve. Include a detailed description of how the control works, who implements it, and the specific steps required for proper execution. Set realistic implementation timelines with clear milestones, and assign ownership to specific individuals who have both the authority and resources to execute it.
Document testing expectations: Your documentation should give special attention to testing frequency and methodology. Specify how often you will verify the control's effectiveness, what evidence you will collect, and what performance standards you expect to see. For example, if you implement a new safety checklist for equipment inspections, document how often supervisors will audit checklist completion, what percentage compliance you consider acceptable, and what corrective actions you will take when performance falls short.
Link controls to the risk register: Connect each control record back to your original risk register using consistent identification numbers or codes. This connection allows you to track whether your mitigation efforts actually reduce risk levels as intended and helps you identify controls that need strengthening or replacement.
Make documentation accessible: Make your documentation accessible to those who need it most. While comprehensive records serve important audit and compliance purposes, frontline workers need simplified, actionable versions they can reference quickly in the field. Consider creating condensed control summaries, visual guides, or mobile-friendly versions that translate complex procedures into practical, step-by-step instructions your teams can actually use when it matters most.
Step 4 – Monitor, Report & Review Operational Risks
Risk management isn't a set-it-and-forget-it process. It demands constant attention, regular check-ins, and ongoing adjustments. Think of it like tending a garden: you plant the seeds (identify risks), water them (implement controls), but then you need to keep weeding, pruning, and adapting as conditions change. This ongoing vigilance aligns perfectly with standard frameworks' "Monitoring and Reporting" elements and the Navy's fifth step of "Supervise."
Effective monitoring rests on four critical pillars that work together to create a comprehensive early warning system:
- Key Risk Indicators (KRIs): Metrics that signal when risk levels are climbing before they become full-blown problems. These might include tracking near-miss frequencies, equipment downtime patterns, or employee turnover rates in high-risk roles.
- Control Testing: Systematically verifying that your safeguards work as designed through regular audits, spot checks, and performance reviews.
- Incident Tracking: Capturing and analyzing actual risk events through effective incident reporting to understand what happened, why it happened, and how to prevent recurrence.
- Near-Miss Reporting: Creating a learning laboratory where close calls that didn't result in harm become valuable intelligence for preventing future incidents.
Monitor KRIs
You should tailor your reporting mechanisms to match the pace and reality of non-desk work environments. Real-time dashboards displaying key risk indicators and trends help managers spot emerging patterns quickly. Photo-enabled SMS reports from the field provide visual evidence of risks or control effectiveness, feeding directly into these dashboards without requiring workers to navigate complex systems or fill out lengthy forms. Executive summaries should follow predictable cadences: weekly operational reviews for immediate risks, monthly strategic assessments for broader patterns, and quarterly deep dives for program effectiveness.
Set Up a System For Review
The review process transforms raw data into actionable intelligence through structured stakeholder meetings, clear escalation procedures for emerging threats, and systematic reassessment of existing risk profiles. Regular cross-team review meetings ensure that lessons learned from incidents and near-misses actually influence future decisions. Managerial walk-throughs become particularly valuable in non-desk environments, where leaders can observe real working conditions and engage directly with frontline teams about risk concerns.
Recognize When The Process Works
Creating a culture that celebrates near miss reporting rather than punishing it generates exponentially more valuable risk intelligence. When employees feel safe reporting close calls, you uncover hidden hazards and process weaknesses before they cause real harm. This monitoring approach creates a continuous feedback loop. Each incident, near-miss, and control test becomes input for refining and improving your entire operational risk management program, making it stronger and more responsive over time.
Step 5 – Iterate & Mature Your Operational Risk Management Program
Your operational risk management program isn't a one-and-done project. It needs to grow and adapt alongside your organization. Think of operational risk management maturity as a journey where each stage builds stronger foundations for protecting your people and operations.
Most organizations progress through three distinct maturity levels:
- Ad-hoc: Basic risk identification and controls that are often reactive, triggered only after incidents occur.
- Defined: Structured processes, clear ownership, and a more proactive approach to managing threats.
- Optimized: Risk management integrates seamlessly with business strategy, uses data-driven insights, and drives continuous improvement across all operations.
A formal Risk and Control Self-Assessment (RCSA) process can accelerate this maturity by systematically evaluating how well your current approach actually works. This isn't just checking boxes. It's honestly assessing whether your controls are preventing the hazards you identified and whether your team is truly prepared for emerging threats.
Several triggers should prompt you to refresh and upgrade your approach. New regulations or compliance requirements often demand updated methods, while mergers and acquisitions bring fresh threat profiles that need assessment. Major incidents or near-misses reveal gaps in your current system, and significant changes in operations or technology can introduce entirely new categories of concern. Even without these catalysts, regular review cycles help ensure your approach stays relevant and effective.
To advance through these maturity levels, start developing more sophisticated metrics that go beyond basic incident counts. Integrate threat considerations into strategic planning sessions and daily operations rather than treating them as separate activities. Monthly "risk retrospectives" create valuable feedback loops where teams can discuss what worked, what didn't, and how to improve next time. Benchmarking against industry best practices also helps identify areas where your approach can evolve to better protect your workforce and operations.
Accelerate Operational Risk Management Success
Building an effective operational risk management program doesn't mean starting from scratch. Three proven frameworks provide tested foundations that save months of trial and error, each designed for different operational realities.
- ISO 31000 works like a Swiss Army knife, flexible enough for any industry. This principles-based approach adapts whether you manage office teams or construction crews across multiple job sites. The real strength lies in how it integrates frontline workers into risk identification instead of treating them as passive rule-followers. Companies using ISO 31000 consistently report easier customization for field conditions while maintaining organizational standards.
- COSO ERM takes the opposite approach: structured, governance-heavy, built for audit trails. Born from accounting needs, it excels in regulated industries where documentation matters as much as results. The downside? Its rigid structure can slow decision-making in fast-moving field operations where waiting for formal approval isn't an option.
- The U.S. DoD Operational Risk Management Framework wins for non-desk environments. Five simple steps (identify hazards, assess hazards, make risk decisions, implement controls, supervise) built for people making real-time decisions in dynamic settings. Construction, logistics, healthcare, and field services find this approach fits naturally into their daily workflows because designers created it for operational reality, not boardroom presentations.
Your technology stack should match your framework choice and team complexity. Enterprise GRC software delivers comprehensive capabilities but demands significant investment and training time. Simple spreadsheets work for smaller operations, while SMS platforms like Yourco bridge the middle ground, enabling instant field reporting without requiring technical expertise from workers who spend their days away from computers.
Most successful organizations don't choose just one framework. They blend approaches, using ISO 31000 or the DoD's operational risk management for daily operations while applying COSO structure for executive reporting. This hybrid strategy captures practical field benefits while meeting broader oversight requirements, offering the best of both worlds without forcing artificial choices.
Operational Risk Management Trends
The landscape of operational risk management is evolving rapidly, driven by technological breakthroughs that are reshaping how you identify, assess, and respond to operational risks in frontline environments. These emerging trends will fundamentally change your approach to managing non-desk teams.
AI-Driven Analytics now enable pattern recognition and anomaly detection that human oversight simply can't match. Machine learning algorithms analyze massive volumes of real-time data from your field operations, automatically flagging deviations that could signal emerging risks. You can spot problems as they develop—whether it's equipment showing early failure signs or worker behavior patterns indicating fatigue or safety risks—instead of waiting for incident reports.
IoT Sensors and Wearables are creating new visibility into frontline operations. Smart helmets in construction, environmental monitors in manufacturing, and location trackers in logistics generate continuous data streams that feed directly into operational risk management systems. When combined with predictive analytics, this technology helps you forecast where and when risks are most likely to materialize.
Consider starting with pilot AI modules for your highest-risk operations while you establish strong data governance practices. SMS and mobile platforms have become critical infrastructure for immediate field reporting, ensuring that even your least tech-savvy workers can instantly communicate risk observations.
Regulatory frameworks are also shifting toward operational resilience rather than mere compliance, with emerging operational risk threats demanding more proactive approaches. Your risk management program needs to demonstrate continuous monitoring and adaptive controls, not just periodic assessments.
Organizations that embrace these technologies now will have significant advantages in managing tomorrow's operational challenges. Start by ensuring your communication systems can handle real-time reporting from the field, then build from there as your data and capabilities mature.
Troubleshooting & FAQ on Operational Risk Management
Q: We have no baseline data; where do we start?
Begin with what you have: incident reports, insurance claims, and employee feedback. Conduct simple risk workshops with frontline teams to identify the most obvious hazards. Even rough estimates of likelihood and impact help prioritize your initial efforts. You can refine your data collection as your program matures.
Q: How do we engage deskless workers in our operational risk management program?
Mobile-enabled incident reporting tools have proven highly effective, with some construction sites seeing a 40% increase in hazard reporting. SMS-based platforms work on any phone and reach workers who might not check email regularly. Appoint 'risk champions' on each shift or team who can advocate for the program and help colleagues report issues.
Q: What if a risk owner leaves the organization?
Document all risk ownership assignments clearly and maintain succession plans. When someone leaves, immediately reassign their risks to another qualified person and update your risk register. Consider having backup owners identified for critical risks to avoid gaps in oversight.
Q: How do we balance operational risk management with operational efficiency?
Focus on the biggest risks first and integrate controls into existing workflows rather than creating separate processes. Use technology to streamline reporting and monitoring. Remember that effective operational risk management actually improves efficiency by preventing costly disruptions and downtime.
Q: How often should we update our risk register?
Review your risk register monthly for high-priority risks and quarterly for lower-priority ones. Trigger immediate updates when incidents occur, operations change significantly, or new regulations emerge. The key is consistency rather than perfection.
Q: How can we measure the ROI of our operational risk management program?
Track both avoided costs (prevented incidents, reduced insurance premiums) and efficiency gains (less downtime, faster incident resolution). Compare your incident rates and associated costs before and after implementing operational risk management controls. The real wins show up in what doesn't happen—the accidents avoided, the compliance violations prevented, and the smooth operations that keep running.
Q: What's the difference between operational risk management and safety management?
Safety management focuses specifically on preventing workplace injuries and health hazards. Operational risk management covers broader business disruptions including technology failures, process breakdowns, compliance issues, and external threats beyond just physical safety. Think of safety as one important piece of the larger operational risk puzzle.
Q: How do we avoid operational risk management becoming just a 'tick-box' exercise?
Keep the focus on real outcomes rather than documentation. Regularly share success stories where risk management prevented actual problems. Involve frontline workers in identifying solutions, not just reporting problems. Celebrate near-miss reporting as learning opportunities rather than blame situations. The moment your team stops seeing the value, you've lost the program's effectiveness.
Building a Safer, More Resilient Operation through Operational Risk Management
When you systematically identify hazards, assess their impact, and implement smart controls, you actively create competitive advantage through operational resilience that keeps your teams safer and your business running smoothly, even when the unexpected hits.
The path forward comes down to three core principles:
- Identify risks before they become problems
- Act quickly when issues surface
- Adapt your approach as conditions change
Your most impactful first step? Open a real-time reporting channel for your frontline teams. Mobile-enabled incident reporting tools have shown a 40% increase in hazard reporting in field environments, transforming your workforce into an early warning system. That simple SMS report from the factory floor or job site could prevent your next major loss.
Yourco makes this transformation seamless with instant communication that reaches every worker, mobile photo documentation that captures evidence in real time, and built-in oversight tools that help managers close the loop fast. No apps to download, no complex systems to learn, just direct communication that works the moment someone spots a risk. With each reporting cycle, your operational risk management program grows smarter, more responsive, and more valuable to your bottom line.
Try Yourco for free today or schedule a demo and see the difference the right workplace communication solution can make in your company.